Edexcel GCSE Computing Paper 1 (2016 spec) exam paper can be downloaded here.
|
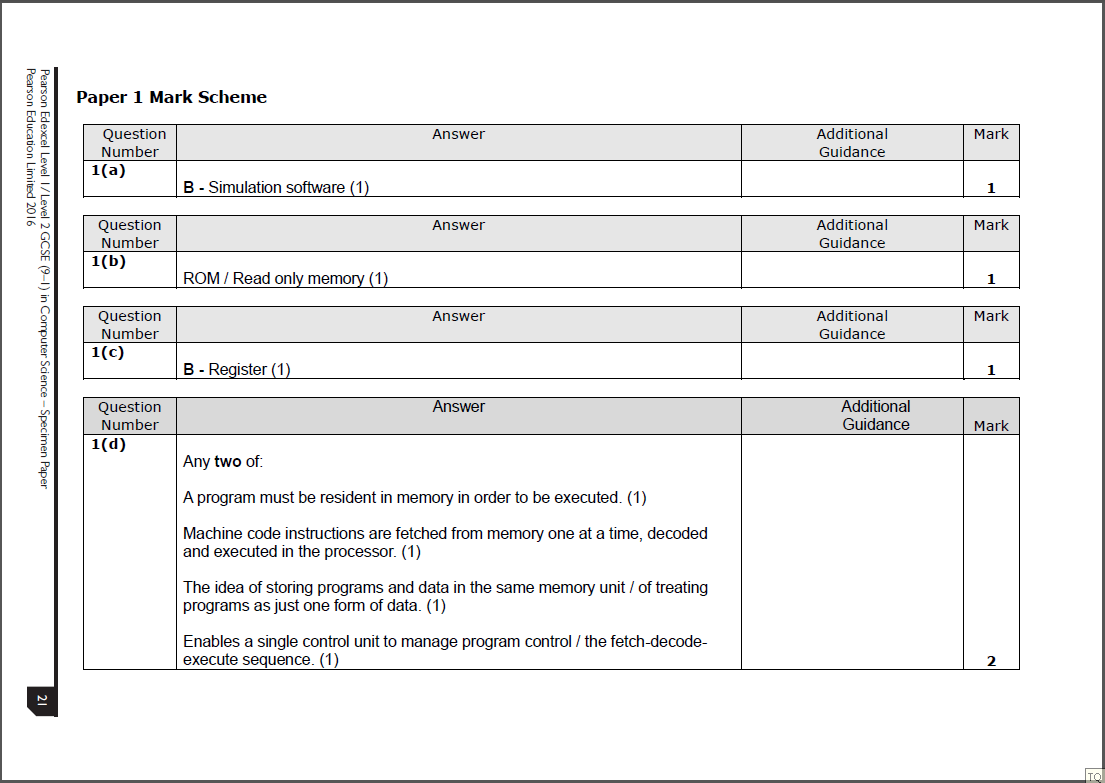
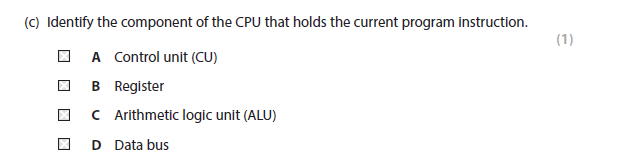
1A Answer
1B answer
1C answer
1D answer
Any two of:
A program must be resident in memory in order to be executed. (1)
Machine code instructions are fetched from memory one at a time, decoded and executed in the processor. (1)
The idea of storing programs and data in the same memory unit / of treating programs as just one form of data. (1)
Enables a single control unit to manage program control / the fetch-decode execute sequence. (1)
More help here - Stored program
A program must be resident in memory in order to be executed. (1)
Machine code instructions are fetched from memory one at a time, decoded and executed in the processor. (1)
The idea of storing programs and data in the same memory unit / of treating programs as just one form of data. (1)
Enables a single control unit to manage program control / the fetch-decode execute sequence. (1)
More help here - Stored program
1E answer
Manages files (1) provides a structure and system / directories for the management of files / allows files to be manipulated (saved, renamed, moved, copied and deleted). (1)
Process management (1) allocating / sharing processor time / resources to running programs. (1)
Manages memory (1) assigning (blocks of) memory to running programs as required. (1)
Manages hardware / drivers (1) to receive data from input devices and to send processed data to output devices. (1)
More help here - OS
Process management (1) allocating / sharing processor time / resources to running programs. (1)
Manages memory (1) assigning (blocks of) memory to running programs as required. (1)
Manages hardware / drivers (1) to receive data from input devices and to send processed data to output devices. (1)
More help here - OS
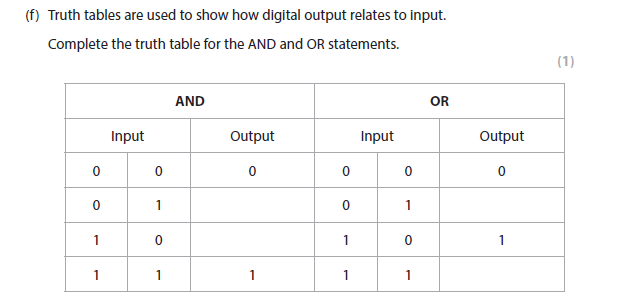
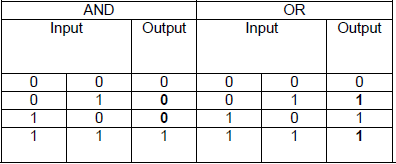
1F answer
2a answer
2B answer
Every node / workstation connects to a central network device, like a hub or switch. (1)
The central network device acts as a router / directs data to the intended peripherals. (1)
All data passes through the central network device on route to its intended destination. (1)
More help here - Network topology
The central network device acts as a router / directs data to the intended peripherals. (1)
All data passes through the central network device on route to its intended destination. (1)
More help here - Network topology
2c answer
Any four from (both must be addressed):
Wireless access point:
Wireless access point transmits and receives radio waves from the tablets.
Enables the tablets to connect to the network using WiFi.
Router:
Directs data packets to / from tables to / from the Internet.
Connects the LAN to the Internet.
Uses routing information stored in its tables to forward data packets.
More help here - Wireless access point
More help here - Router
Wireless access point:
Wireless access point transmits and receives radio waves from the tablets.
Enables the tablets to connect to the network using WiFi.
Router:
Directs data packets to / from tables to / from the Internet.
Connects the LAN to the Internet.
Uses routing information stored in its tables to forward data packets.
More help here - Wireless access point
More help here - Router
2d answer
3a answer
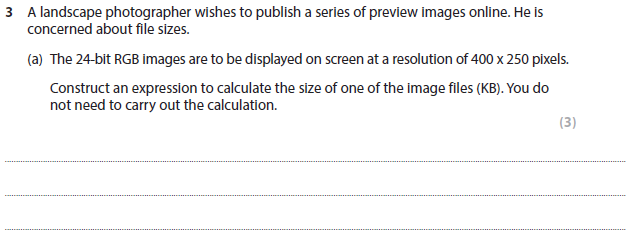
(400 x 250 x 24) / (8 x 1024) (3)
or
400 x 250 x 24 (1) / 8 (1) / 1024 (1)
More help here - File size calculation
or
400 x 250 x 24 (1) / 8 (1) / 1024 (1)
More help here - File size calculation
3b answer
Any two of the following:
File sizes / download times will be reduced. (1)
Some loss of image data / image quality will occur. (1)
JPEGs allow image quality to be fine-tuned / the level of compression to be adjusted. (1)
More help here - Compression
File sizes / download times will be reduced. (1)
Some loss of image data / image quality will occur. (1)
JPEGs allow image quality to be fine-tuned / the level of compression to be adjusted. (1)
More help here - Compression
3c answer
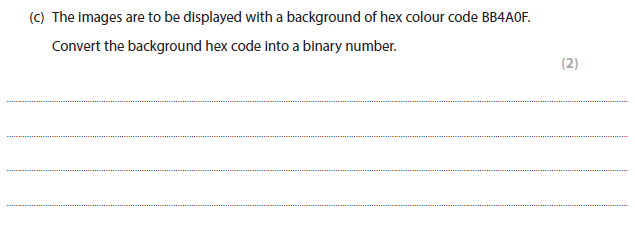
1011 1011 0100 1010 0000 1111 (1 mark for 24-bit response, 1 mark for all correct).
More help here - Hex to binary
More help here - Hex to binary
3D answer
Shorthand form that is easier for humans to read (1)
and is likely to reduce errors when specifying colours / reduces potential for mixing up the 0s and 1s.(1)
More help here - Hex
and is likely to reduce errors when specifying colours / reduces potential for mixing up the 0s and 1s.(1)
More help here - Hex
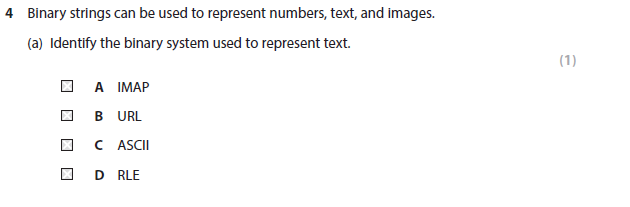
4a answer
4b answer
An explanation that makes reference to the following point:
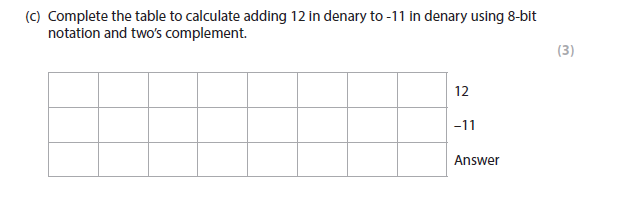
Overflow is the result of a binary addition where the sum exceeds the word length of the CPU / computer / maximum number of bits the CPU can process at one time / available storage space. (1)
Plus one from: The computer ignores the overflow digit. (1)
This could cause errors in further calculations. (1)
More help here - Overflow
Overflow is the result of a binary addition where the sum exceeds the word length of the CPU / computer / maximum number of bits the CPU can process at one time / available storage space. (1)
Plus one from: The computer ignores the overflow digit. (1)
This could cause errors in further calculations. (1)
More help here - Overflow
4c answer
4d answer
The value of the number is halved / the number is divided by 2. (1)
The sign bit is retained. (1)
More help here - Binary shift
The sign bit is retained. (1)
More help here - Binary shift
4e answer
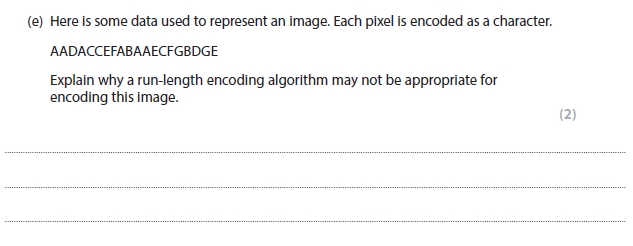
This sequence has very few repeated patterns (1), therefore using a RLE will not lead to a significant reduction in the file size / not compress the image very much. (1)
More help here - RLE
More help here - RLE
5ai answer
5aii answer
Compilation / Use a compiler / Interpretation / Use an interpreter. (1)
More help here - Translator
More help here - Translator
5b answer
An explanation that makes reference to two of the following points:
Non specialist (1) - can be developed without knowledge of hardware / architecture. (1)
Accessible (1) - straightforward to read as closer to natural language. (1)
Availability of library functions (1) – both built in and available from third parties / usually tested and well proven. (1)
Portability (1) - the app will be portable because the source could be translated to run on various types of computer. (1)
Non specialist (1) - can be developed without knowledge of hardware / architecture. (1)
Accessible (1) - straightforward to read as closer to natural language. (1)
Availability of library functions (1) – both built in and available from third parties / usually tested and well proven. (1)
Portability (1) - the app will be portable because the source could be translated to run on various types of computer. (1)
5c answer
Indicative content:
Monetary cost:
Open source software is often developed by a non-profit community and is free to use.
Proprietary software is usually purchased from a software company who licenses its use.
Availability of source code:
Open source software can be distributed and modified without permission. Anyone can fix bugs and create updates, without any need to wait for a new release.
Availability of support:
Open source software usually has help available from the community of experts who are interested and contribute to forums.
Proprietary development software will not have issues with ongoing parallel developments as updates / changes are controlled, avoiding confusion between versions.
Proprietary development software will be supported by the originators.
Stability, reliability, suitability
Open source is based on open standards that are accessible to everyone - avoids compatibility problems.
Open source code is continually analysed by a large community of experts and therefore is stable / reliable.
Proprietary development software will be less vulnerable to malicious users who could exploit the level of access provided to open source code.
More help here - Open source
Monetary cost:
Open source software is often developed by a non-profit community and is free to use.
Proprietary software is usually purchased from a software company who licenses its use.
Availability of source code:
Open source software can be distributed and modified without permission. Anyone can fix bugs and create updates, without any need to wait for a new release.
Availability of support:
Open source software usually has help available from the community of experts who are interested and contribute to forums.
Proprietary development software will not have issues with ongoing parallel developments as updates / changes are controlled, avoiding confusion between versions.
Proprietary development software will be supported by the originators.
Stability, reliability, suitability
Open source is based on open standards that are accessible to everyone - avoids compatibility problems.
Open source code is continually analysed by a large community of experts and therefore is stable / reliable.
Proprietary development software will be less vulnerable to malicious users who could exploit the level of access provided to open source code.
More help here - Open source
6ai answer
To provide a platform for users to run applications (1) and enable users
to access network resources provided by the server. (1)
A client workstation accesses data from a server by making a
connection to the server (1) and issuing a service request. (1)
More help here - Client-server
to access network resources provided by the server. (1)
A client workstation accesses data from a server by making a
connection to the server (1) and issuing a service request. (1)
More help here - Client-server
6aii answer
6b answer
Any three from:
Data is stored digitally in a grid of transistors. (1)
A save operation uses an electrical charge to create binary string. (1)
Changing the value of some transistors from 1 to 0. (1)
Cells are filled with electrons which represent 0s and empty cells represent 1s. (1)
It uses semi-conductor chips called NAND flash. (1)
More help here - SSD
Data is stored digitally in a grid of transistors. (1)
A save operation uses an electrical charge to create binary string. (1)
Changing the value of some transistors from 1 to 0. (1)
Cells are filled with electrons which represent 0s and empty cells represent 1s. (1)
It uses semi-conductor chips called NAND flash. (1)
More help here - SSD
6c answer
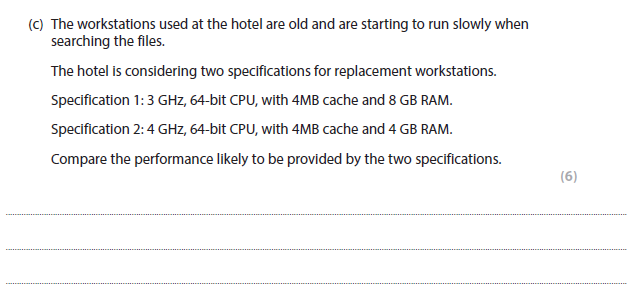
Indicative content:
Specification 2 has a higher clock speed and therefore will be able to deal with a greater number of instructions / cycles per second with the effect that processing will be faster than for Specification 1.
Because of the higher clock speed the CPU in Specification 2 will use more energy and create more heat than the CPU in Specification 1.
The CPU cache memories and the bandwidths are the same.
Specification 1 has more RAM / a larger memory and will therefore be able to handle more programs and operations at the same time. The larger memory will reduce the extent of swapping with virtual memory / secondary storage which will go some way to offset the benefit provided by the greater clock speed of Specification 2.
More help here - Clock speed
Specification 2 has a higher clock speed and therefore will be able to deal with a greater number of instructions / cycles per second with the effect that processing will be faster than for Specification 1.
Because of the higher clock speed the CPU in Specification 2 will use more energy and create more heat than the CPU in Specification 1.
The CPU cache memories and the bandwidths are the same.
Specification 1 has more RAM / a larger memory and will therefore be able to handle more programs and operations at the same time. The larger memory will reduce the extent of swapping with virtual memory / secondary storage which will go some way to offset the benefit provided by the greater clock speed of Specification 2.
More help here - Clock speed
7a answer
HTTP provides the set of rules / mutual understanding / defines how messages are formatted and transmitted (1) that enables the exchange of data between a client / browser and a web server. (1)
More help here - HTTP
More help here - HTTP
7bi answer
7bii answer
When a client / your browser connects to a website via HTTPS the browser and
web server send each other unique codes which are used to encrypt any
transmitted data / the data is encrypted before transmission. (1)
If the data is intercepted by a third party / hacker it will not have any meaning. It
can only be read / decrypted using the unique decryption key provided. (1)
More help here - HTTPS
web server send each other unique codes which are used to encrypt any
transmitted data / the data is encrypted before transmission. (1)
If the data is intercepted by a third party / hacker it will not have any meaning. It
can only be read / decrypted using the unique decryption key provided. (1)
More help here - HTTPS
7c answer
An ethical hacker is a computer / networking expert who works on behalf of the system owners (carries out penetration testing) (1) to find security vulnerabilities that a malicious hacker could exploit. (1) They document vulnerabilities / provide advice on how to fix them. (1)
More help here - White hat
More help here - White hat
7d answer
8a answer
8b answer
Ethernet protocols define standards for network cabling / types of cabling used at the physical layer (1) and corresponding transmission speeds. (1) At the data link layer Ethernet protocols describe how network devices can format data for transmission (1) using frames / packets. (1)
More help here - Ethernet
More help here - Ethernet
8c answer
Each layer of the TCP/IP model prepares data for transmission from one computer to another. (1)
Data is sent downwards from the application (application layer) (1)
through protocol stack to the physical media (physical layer). (1)
At each stage information is added to the packet such as destination address, source address, protocol, routing information, error correction. (1)
At the receiving computer the packet passes through the layers in reverse. (1)
There are four layers in a simple TCP/IP model (Application layer, Transport layer, Network layer, Data link layer). (1)
More help here - TCP/IP
Data is sent downwards from the application (application layer) (1)
through protocol stack to the physical media (physical layer). (1)
At each stage information is added to the packet such as destination address, source address, protocol, routing information, error correction. (1)
At the receiving computer the packet passes through the layers in reverse. (1)
There are four layers in a simple TCP/IP model (Application layer, Transport layer, Network layer, Data link layer). (1)
More help here - TCP/IP
Loading Paper 1 (Sample 1)