1A Answer
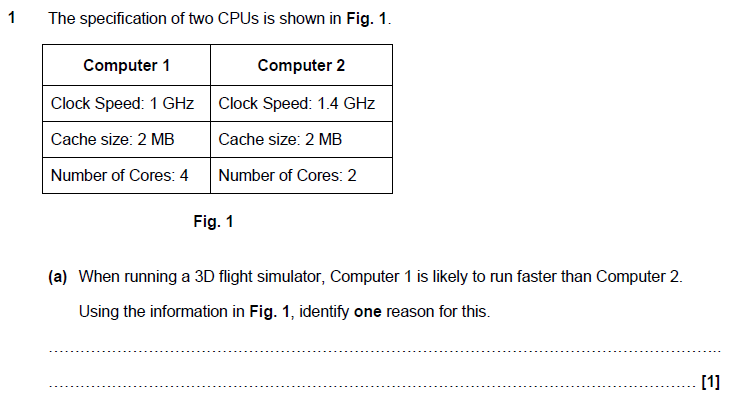
It has more cores (1)
More help here -
More help here -
1B answer
RAM
SSD
HDD
Graphics card (GPU)
Motherboard
Sound card
More help here -
SSD
HDD
Graphics card (GPU)
Motherboard
Sound card
More help here -
1C answer
• data is transferred faster (1)…
• …which makes a CPU more efficient (1)
• It is faster to transfer to and from cache (1)…
• …than transferring to and from RAM (1).
More help here -
• …which makes a CPU more efficient (1)
• It is faster to transfer to and from cache (1)…
• …than transferring to and from RAM (1).
More help here -
1d answer
• An instruction is fetched from memory
• The instruction is then decoded
• The decoded instruction is then executed so that the CPU performs continuously
• The process is repeated
• The program counter is incremented
• The instruction is transferred to the MDR
• The address of the instruction to be fetched is placed in the MAR
More help here -
• The instruction is then decoded
• The decoded instruction is then executed so that the CPU performs continuously
• The process is repeated
• The program counter is incremented
• The instruction is transferred to the MDR
• The address of the instruction to be fetched is placed in the MAR
More help here -
2a answer
• Long term/non-volatile storage of data/files
• External/auxiliary storage of data
More help here -
• External/auxiliary storage of data
More help here -
2b answer
• Optical
• Magnetic
• Solid state
More help here -
• Magnetic
• Solid state
More help here -
2c answer
Four characteristics from:
• Capacity/size
• Speed
• Portability
• Durability
• Reliability
• Cost
More help here -
• Capacity/size
• Speed
• Portability
• Durability
• Reliability
• Cost
More help here -
3a answer
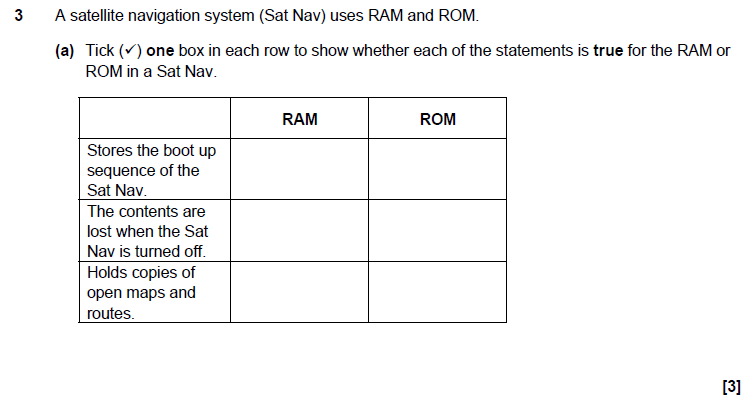
Stores the boot up sequence of the Sat Nav = ROM
The contents are lost when the Sat Nav is turned off = RAM
Holds copies of open maps and routes = RAM
More help here -
The contents are lost when the Sat Nav is turned off = RAM
Holds copies of open maps and routes = RAM
More help here -
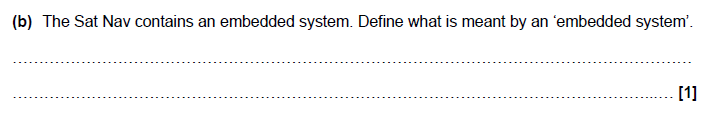
3B answer
• A computer system that is built into another device
More help here -
More help here -
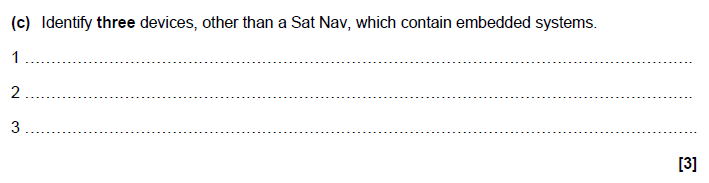
3c answer
Three devices from:
e.g.
• Dishwasher
• MP3 player
• Washing machine
• Mobile phone
• Manufacturing equipment
More help here -
e.g.
• Dishwasher
• MP3 player
• Washing machine
• Mobile phone
• Manufacturing equipment
More help here -
4A answer
- The height of the wave is measured/sampled (at regular/set intervals)
- Turned into/stored as binary
More help here -
4B answer
- The quality will improve
- The file size will increase
More help here -
5a answer
203
More help here -
More help here -
5b answer
0011 0010
More help here -
More help here -
5c answer
- Divide the number by 4
- Loses precision
More help here -
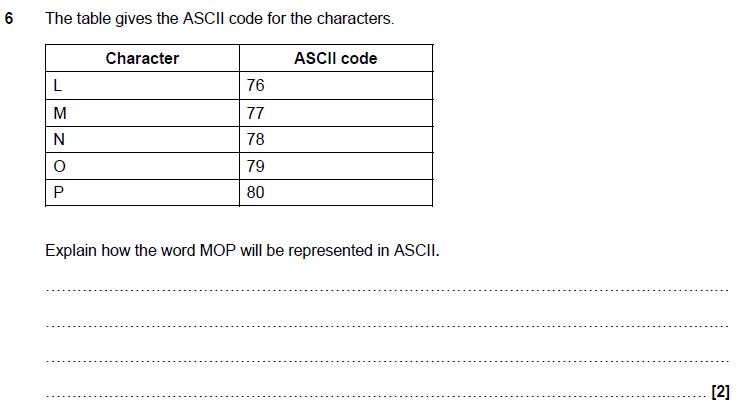
6 answer
1 mark per bullet
More help here -
- each character from MOP has its ASCII code stored in the order written
- 77 79 80 (MOP)
- ASCII code converted to 8-bit binary number
More help here -
7A answer
• A set of rules for communication
More help here -
More help here -
7bi answer
• A division of network functionality
More help here -
More help here -
7bii answer
• It is self-contained (1)…
• …it allows different developers to concentrate on one aspect of the network
(1)
• A layer can be taken out and edited without affecting other layers (1)…
• …it promotes interoperability between vendors and systems (1)
More help here -
• …it allows different developers to concentrate on one aspect of the network
(1)
• A layer can be taken out and edited without affecting other layers (1)…
• …it promotes interoperability between vendors and systems (1)
More help here -
7c answer
• It is easy to add a new node or device
• Fewer data collisions can occur
• If a node or device fails it does not affect the rest of the network
• A signal does not need to be transmitted to all computers in the network
More help here -
• Fewer data collisions can occur
• If a node or device fails it does not affect the rest of the network
• A signal does not need to be transmitted to all computers in the network
More help here -
8a answer
• Firewall (1 – AO2 1a) prevents unauthorised access (1 – AO2 1b)
• Anti-malware (1 – AO2 1a) removes viruses/spyware from infecting the system (1 – AO2 1b)
• Encryption (1 – AO2 1a) any intercepted data is rendered useless (1 – AO2 1b)
• User access levels (1 – AO2 1a) users have restricted access (1 – AO2 1b)
• Network policies (1 – AO2 1a) rules that define acceptable use (1 – AO2
1b)
More help here -
• Anti-malware (1 – AO2 1a) removes viruses/spyware from infecting the system (1 – AO2 1b)
• Encryption (1 – AO2 1a) any intercepted data is rendered useless (1 – AO2 1b)
• User access levels (1 – AO2 1a) users have restricted access (1 – AO2 1b)
• Network policies (1 – AO2 1a) rules that define acceptable use (1 – AO2
1b)
More help here -
8b answer
• Brings in files via any medium (1 – AO2 1a)…
• …not allowing/stopping external devices being used on the network (1 – AO2 1b)
• Downloading infected files from the internet (1 – AO2 1a)…
• …blocking/restricting access to insecure websites (1 – AO2 1b)
• Allowing physical access to the surgery’s network (1 – AO2 1a)…
• …locking of doors/key cards/any physical security procedure (1 – AO2 1b)
• Sending/sharing sensitive data with third parties (1 – AO2 1a)…
• … blocking/restricting access to USB ports/email/internet/printing (1 – AO2 1b)
More help here -
• …not allowing/stopping external devices being used on the network (1 – AO2 1b)
• Downloading infected files from the internet (1 – AO2 1a)…
• …blocking/restricting access to insecure websites (1 – AO2 1b)
• Allowing physical access to the surgery’s network (1 – AO2 1a)…
• …locking of doors/key cards/any physical security procedure (1 – AO2 1b)
• Sending/sharing sensitive data with third parties (1 – AO2 1a)…
• … blocking/restricting access to USB ports/email/internet/printing (1 – AO2 1b)
More help here -
9a answer
• Orders have been saved onto the system as they order food and then deleted once processed (1)
• Once other orders have been made, new files are created (1) which may be bigger than the spaces left by the deleted files (1)
• The order files are split up (1)
More help here -
• Once other orders have been made, new files are created (1) which may be bigger than the spaces left by the deleted files (1)
• The order files are split up (1)
More help here -
9b answer
• Files on the hard disk drive are moved (1)
• Empty spaces collected together (1)
• Files are moved to be stored together (1)
• Fewer disc accesses are needed (1)
More help here -
• Empty spaces collected together (1)
• Files are moved to be stored together (1)
• Fewer disc accesses are needed (1)
More help here -
10a answer
• The computers are geographically remote/ distanced/ more than a mile apart
• Communication medium is not owned by the law firm
More help here -
• Communication medium is not owned by the law firm
More help here -
10b answer
Two advantages from:
• It would offer additional storage (1) so the company can take on more cases (1)
• It is a very efficient method of backing up data (1) and so saves the firm time and money (1)
• It would allow their employees to work from anywhere (1) so they can take cases from other countries (1)
• It is environmentally friendly (1)
• Easy to increase availability of storage (1)
• You don’t need specialist network skills (1) so the firm don’t need to employ more staff (1)
• The third party provides security (1) so the company saves money on staff and software/hardware (1)
• The third party provides backup (1) so the company saves money on staff and software/hardware (1)
• Cheaper as don’t need own infrastructure (1)
Each advantage needs to be contextualised to gain 2 marks.
More help here -
• It would offer additional storage (1) so the company can take on more cases (1)
• It is a very efficient method of backing up data (1) and so saves the firm time and money (1)
• It would allow their employees to work from anywhere (1) so they can take cases from other countries (1)
• It is environmentally friendly (1)
• Easy to increase availability of storage (1)
• You don’t need specialist network skills (1) so the firm don’t need to employ more staff (1)
• The third party provides security (1) so the company saves money on staff and software/hardware (1)
• The third party provides backup (1) so the company saves money on staff and software/hardware (1)
• Cheaper as don’t need own infrastructure (1)
Each advantage needs to be contextualised to gain 2 marks.
More help here -
10c answer
Two disadvantages from:
• You need a constant internet connection (1) which lawyers who travel a lot may not always have (1)
• Reliant on third party to carry out security procedures (1) but the firm are still legally responsible if things go wrong (1)
• Reliant on third party for back up connection (1)
• Data stored in the Cloud will be vulnerable to hacking and other threats (1)
which the firm have no control over (1)
• Issues regarding data ownership (1)
• Implications of Data Protection Act (1)
Each disadvantage needs to be contextualised to gain 2 marks
More help here -
• You need a constant internet connection (1) which lawyers who travel a lot may not always have (1)
• Reliant on third party to carry out security procedures (1) but the firm are still legally responsible if things go wrong (1)
• Reliant on third party for back up connection (1)
• Data stored in the Cloud will be vulnerable to hacking and other threats (1)
which the firm have no control over (1)
• Issues regarding data ownership (1)
• Implications of Data Protection Act (1)
Each disadvantage needs to be contextualised to gain 2 marks
More help here -
10d answer
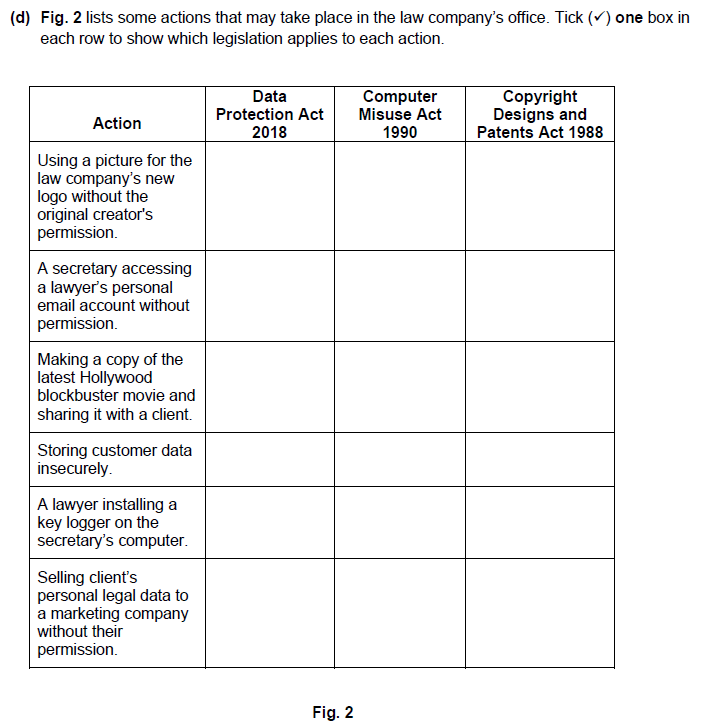
Using a picture for the law company’s new logo without the original creator’s permission = CDP act
A secretary accessing a lawyer’s personal email account without permission = CM act
Making a copy of the latest Hollywood blockbuster movie and sharing it with a client = CDP act
Storing customer data insecurely = DP act
A lawyer installing a key logger on the secretary’s computer = CM act
Selling client’s personal data to a marketing company without their permission = DP act
More help here -
A secretary accessing a lawyer’s personal email account without permission = CM act
Making a copy of the latest Hollywood blockbuster movie and sharing it with a client = CDP act
Storing customer data insecurely = DP act
A lawyer installing a key logger on the secretary’s computer = CM act
Selling client’s personal data to a marketing company without their permission = DP act
More help here -
11 answer
The following is indicative of possible factors/evidence that candidates may refer to but is not prescriptive or exhaustive:
Indicative Content:
Smartphone users
• Can adversely affect people in this country and abroad:
o health issues
o financially
o socially
o culturally
Cultural issues
• Desire/need to own newest device
• …to fit in with peers
• May have new features that users require for work/leisure
Environmental issues
• The type of devices that are disposed of
• Modern phones poorly designed for durability
• Phones’ hardware not upgradeable/replaceable
• Reference to e-waste (people dispose of their devices in landfill even if they are in good working order)
• Some equipment is also sent abroad to be disposed of
• Leads to excessive landfill (in this country and/or abroad, e.g. Africa and Asia)
• Toxic waste released into land, ground water, air (in this country and/or abroad, e.g. Africa and Asia)
• Waste of resources
• Precious metals in phones
Ethical issues
• Contributes to ill health
• Contributes to the digital divide
• Contributes to social divide
• Problem of confidential data stored on the devices
• Puts social pressure on parents to pay for their children to upgrade
• Puts social pressure on the public to upgrade
• Can lead to bullying of those who cannot afford the latest technology
• Phone manufacturers intentionally designing fragile phones so they need to be replaced more often
• High cost of new devices.
More help here -
Indicative Content:
Smartphone users
• Can adversely affect people in this country and abroad:
o health issues
o financially
o socially
o culturally
Cultural issues
• Desire/need to own newest device
• …to fit in with peers
• May have new features that users require for work/leisure
Environmental issues
• The type of devices that are disposed of
• Modern phones poorly designed for durability
• Phones’ hardware not upgradeable/replaceable
• Reference to e-waste (people dispose of their devices in landfill even if they are in good working order)
• Some equipment is also sent abroad to be disposed of
• Leads to excessive landfill (in this country and/or abroad, e.g. Africa and Asia)
• Toxic waste released into land, ground water, air (in this country and/or abroad, e.g. Africa and Asia)
• Waste of resources
• Precious metals in phones
Ethical issues
• Contributes to ill health
• Contributes to the digital divide
• Contributes to social divide
• Problem of confidential data stored on the devices
• Puts social pressure on parents to pay for their children to upgrade
• Puts social pressure on the public to upgrade
• Can lead to bullying of those who cannot afford the latest technology
• Phone manufacturers intentionally designing fragile phones so they need to be replaced more often
• High cost of new devices.
More help here -