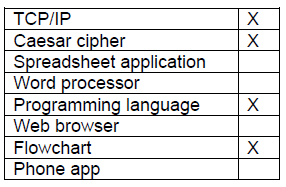
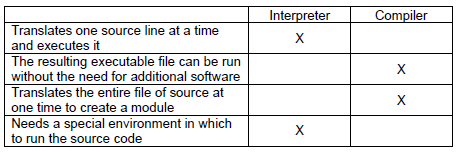
1Ai Answer
8
More help here -
More help here -
1aii answer
28
2 x 2 x 2 x 2 x 2 x 2 x 2 x 2
24 x 24
More help here -
2 x 2 x 2 x 2 x 2 x 2 x 2 x 2
24 x 24
More help here -
1aiii answer
1024, 2 to the power of 10
1024 x 1024, 1024 to the power of 2, 1048576, 2 to the power of 20
More help here -
1024 x 1024, 1024 to the power of 2, 1048576, 2 to the power of 20
More help here -
1aiv answer
1024 x 1024 x 1024
1024 to the power of 3
2**10 x 2**10 x 2**10
2**30
More help here -
1024 to the power of 3
2**10 x 2**10 x 2**10
2**30
More help here -
1v answer
Instructions
More help here -
More help here -
1bi answer
78
More help here -
More help here -
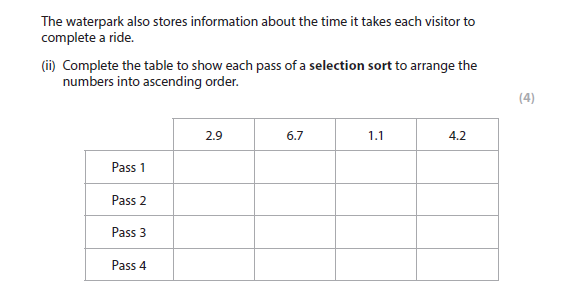
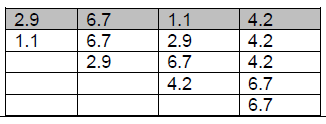
1bii answer
Answer must be given to 8-bits
One mark for each correct 4-bits (nibble)
0011 1111
3 = 0011 F = 1111
More help here -
One mark for each correct 4-bits (nibble)
0011 1111
3 = 0011 F = 1111
More help here -
1biii answer
As a shorthand for binary
Easier for humans to read than binary
Shorter visual representation than binary
More help here -
Easier for humans to read than binary
Shorter visual representation than binary
More help here -
1ci answer
Bits per second
More help here -
More help here -
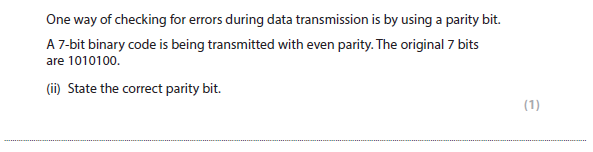
1cii answer
1 is the parity bit
More help here -
More help here -
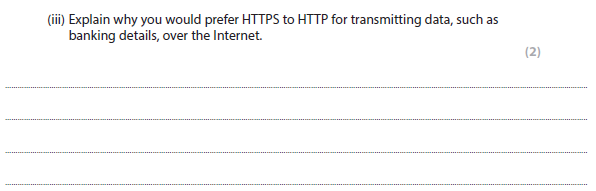
1ciii answer
Any two of:
More help here -
- HTTP is not secure and/or not encrypted so anyone who captures the data can easily read it.
- HTTPS is secure and/or encrypted.
- No one can decrypt/unscramble/decipher information sent over HTTPS, unless they have the correct key.
- No unauthorised person can decrypt the data.
More help here -
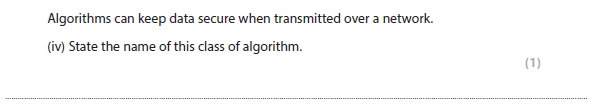
1civ answer
Encryption
More help here -
More help here -
2ai answer
- Sharing Internet connection
- Share peripherals (printer, scanner, speakers, …)
- Cost savings by sharing hardware/software
- Share data (files, database, …)
- Transfer files between computers
- Collaboration on projects
- Communicating (email, instant messaging, chat, …)
- Data can be backed up from one location
- Network login to control access to all machines on network
- Software installed to individual machines from a central location
- Monitor usage of hardware/software
- Monitor behaviours of users
More help here -
2aii answer
An example from any two of the following rows:
More help here -
- copper cable, twisted-pair, co-axial cable or mains network (networking over mains power line in building)
- fibre optic cable
- wireless, infrared or microwave
More help here -
2bi answer
Any one of:
More help here -
- To allow connected machines to communicate
- To provide the rules of communication between two networked devices
More help here -
2bii answer
Any two of:
More help here -
- MAC addresses provide a permanent physical identification of each device on a network
- MAC addresses are unique for each device
- MAC address are assigned at manufacture
- MAC addresses never change
- MAC addresses work at the hardware level
- MAC addresses work at the data link layer (level 2) of the OSI model
More help here -
2biii answer
Any two of:
More help here -
- IP address identifies a device on a network
- IP addresses may be static or dynamic
- IP addresses may change on each reconnection to a network
- Dynamic IP addresses are assigned when connecting to a network
- Usually are mapped to domain names like “www.google.co.uk”
- IP addresses work at the network level (level 3) of the OSI model
- IP addresses provide a way to represent hierarchical organisations of machines
More help here -
2c answer
Any one of
More help here -
- input/output
- resource allocation
- process management
- network management
- user management
More help here -
3ai answer
B – Actuators
More help here -
More help here -
3aii answer
3bi answer
Any one of:
More help here -
- Computer Misuse Act
- Data Protection Act
More help here -
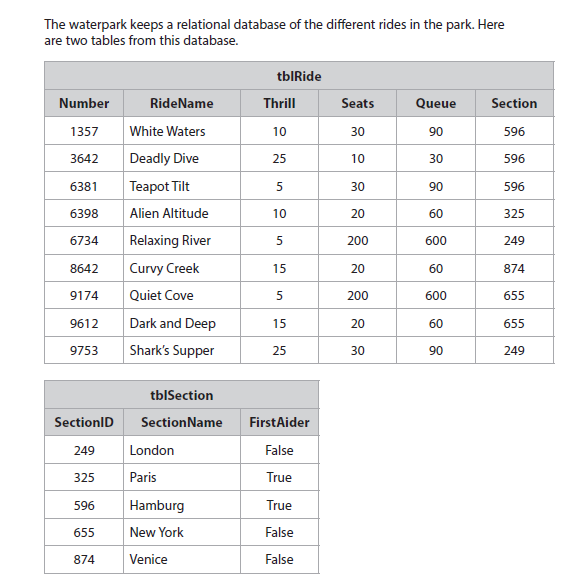
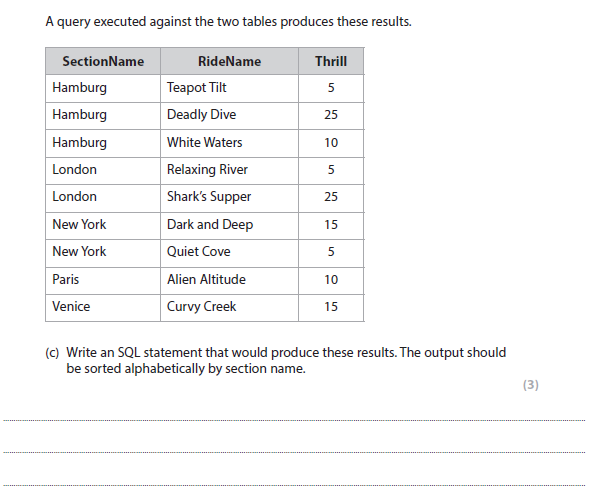
3c answer
One mark for each of:
SELECT (SectionName) FROM tblSection (RideName, Thrill) FROM tblRide
WHERE SectionID = Section
ORDER BY SectionName;
SELECT (SectionName, RideName, Thrill)
FROM tblSection, tblRide,
WHERE SectionID = Section
ORDER BY SectionName;
SELECT (SectionName, RideName, Thrill)
FROM tblSection, tblRide,
WHERE tblSection.SectionID = tblRide.Section
ORDER BY SectionName;
SELECT SectionName, tblRide.RideName, tblRide.Thrill
FROM tblSection
JOIN SectionID=tblRide.Section
ORDER BY SectionName;
SELECT [tblSection].SectionName, [tblRide].RideName, [tblRide].Thrill
FROM tblSection
INNER JOIN tblRide ON [tblSection].SectionID=[tblRide].Section
ORDER BY [tblSection].SectionName;
More help here -
- Indication of 2 tables (SELECT, FROM)
- Indication of field equivalence “SectionID = Section” (JOIN, WHERE)
- Indication of ordering (ORDER BY)
SELECT (SectionName) FROM tblSection (RideName, Thrill) FROM tblRide
WHERE SectionID = Section
ORDER BY SectionName;
SELECT (SectionName, RideName, Thrill)
FROM tblSection, tblRide,
WHERE SectionID = Section
ORDER BY SectionName;
SELECT (SectionName, RideName, Thrill)
FROM tblSection, tblRide,
WHERE tblSection.SectionID = tblRide.Section
ORDER BY SectionName;
SELECT SectionName, tblRide.RideName, tblRide.Thrill
FROM tblSection
JOIN SectionID=tblRide.Section
ORDER BY SectionName;
SELECT [tblSection].SectionName, [tblRide].RideName, [tblRide].Thrill
FROM tblSection
INNER JOIN tblRide ON [tblSection].SectionID=[tblRide].Section
ORDER BY [tblSection].SectionName;
More help here -
3e answer
- Implemented in hardware using quantum states of a physical particle such as the spinning direction of atoms, electrons, or magnetic fields
- Qubits can be 1, 0, anything between, or both simultaneously (superposition)
- Current materials need super cooling for implementing quantum computing
- Can be used to perform millions of calculations in parallel
- Have the potential to massively speed up processing in computers
- Are very expensive because of the hardware needed
- Suitable applications in security, vision recognition, and medical diagnosis
- May be used to solve problems not considered solvable by current computers (intractable)
- Could development costs be better spent?
- May lead to current encryption algorithms being easily broken
More help here -
4ai answer
Any two of:
More help here -
- Populations are represented by many individuals.
- Individuals can be programmed with a simple set of rules.
- In the real world, most individual organisms behave according to internal rules, not in conjunction with other individuals
- Individual interactions based on the rules generate whole system/colony behaviours.
- Changing the rules results in different behaviours, which may lead to new understanding.
- Understanding of behaviours may be applied in new and different contexts
- Swarm behaviours are simulated with this technique.
- Individuals cooperate to achieve a result
- Individuals coordinate activities to achieve a result
More help here -
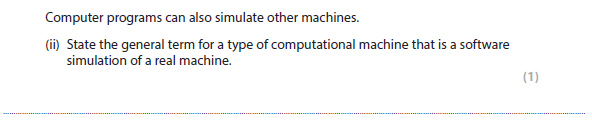
4aii answer
Virtual Machine
More help here -
More help here -
4bi answer
Any four of:
More help here -
- Uses a mantissa/fractional/significand part
- Uses an exponent part
- Uses exponent to shift decimal to correct place in mantissa/fraction/significand
- Binary digits of 1 on right of decimal (fractional part) represents ½, ¼, …
- Binary digits of 1 on left of decimal represents 1, 2, 4, 8, …
- Ones on each side of decimal are summed to get a value
More help here -
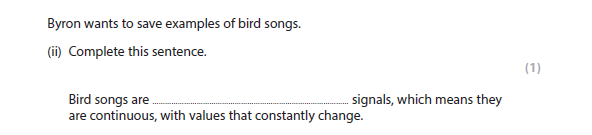
4bii answer
Analogue
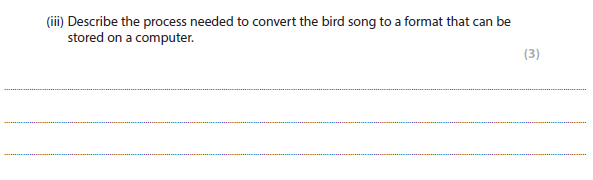
4biii answer
Any three of:
- The height/amplitude of the signal is measured.
- The sampling/measuring takes place at given times/intervals.
- The sampled value is saved.
- This sampling and saving continues along the whole signal.
- The more frequent the samples, the more true the digital representation is to the original analogue signal.
- The sampled values are a stepped representation of the original analogue curve.
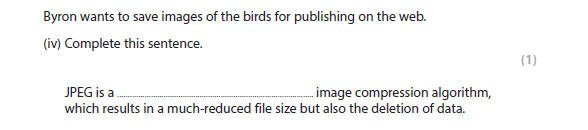
4biv answer
Lossy
4bv answer
Intellectual property (IP)
4c answer
Any four of:
- Phone can be located if reported stolen
- Parents can track where their children are
- Convicted law breakers can be tracked
- Dementia patients can be located if they wander from home
- Employees could track movement of employees, like delivery drivers
- Emergency services can find you, even if you can’t talk on the phone
- Movements tied to other systems such as transport to be used as input to traffic control algorithms
- Can be offered services/information relevant to location
- Data may be collected and stored
- Use of information may be seen as an invasion of privacy
- Is it ethical to track vulnerable people (children, dementia)?
- Is it ethical to track law breakers (sex offenders, parolees)?
- Who should be allowed access to the collected position data?
- Could law enforcement be granted automatic access or should they need a court order?
- Employees, with a mobile phone, would still be tracked even when they weren’t working for the company (evenings, holidays)
5a answer
Any two of:
- Easy to search using queries
- Easy to create reports
- Easy to amend/correct/delete entries
- Easy to keep data backed up and secure
- Keep organised
5bi answer
Input (any one of):
Output (any one of):
- Gender of the cat
- Male, Female, M, F
Output (any one of):
- Building number
- 16, 32, building 16, building 32
- Error message
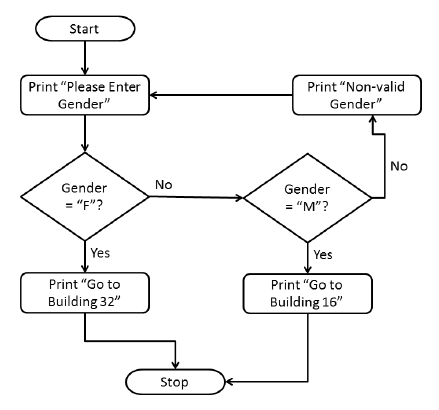
5bii answer
One mark for each of:
- Start symbol and one flow arrow in correct direction
- Decision diamond with Gender=F, Yes/No labels, Yes=Bldg 32
- Decision diamond with Gender=M, Yes/No labels, Yes=Bldg 16
- Error message indicating non-valid entry, reconnection to original print/start
- Stop symbol and appropriate flow arrow(s) in correct direction
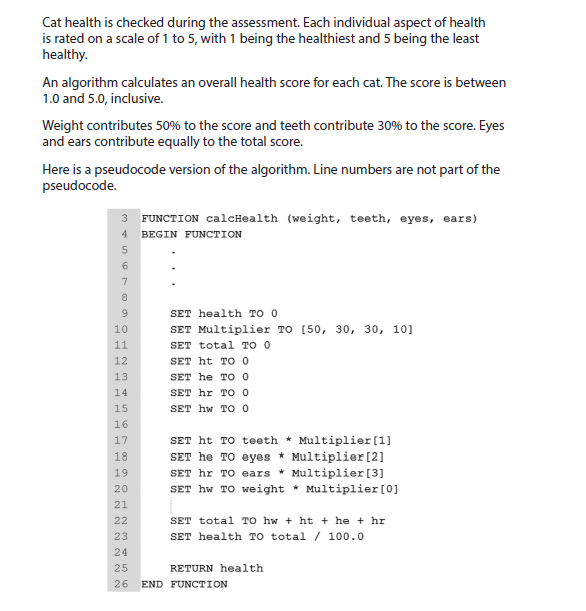
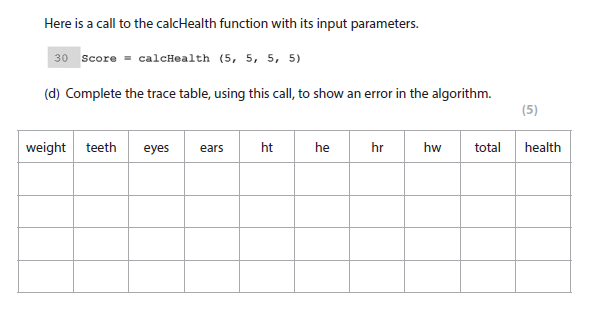
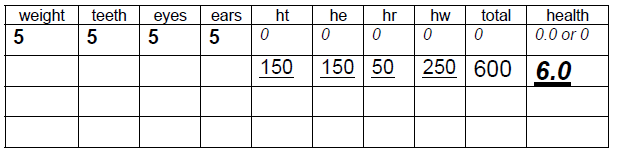
5d answer
One mark for each of:
- weight, teeth, eyes, ears initialised to 5
- ht, he, hr, hw, total initialised to 0; health initialised to 0 or 0.0
- ht, he, hr, hw set to 150, 150, 50, 250 as result of multiplication
- total set to 600 as result of addition
- health set to 6.0 as result of division; must be real number; 6 is not awardable
Loading Sample assessment 2