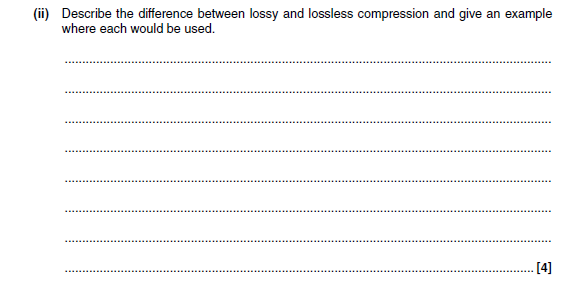1A Answer
Storage: device used to store data (in binary format for processing later)
Input: device used to enter data into the computer
Output: device used to present information/the result of processing to the user
More help here - More here
Input: device used to enter data into the computer
Output: device used to present information/the result of processing to the user
More help here - More here
1B answer
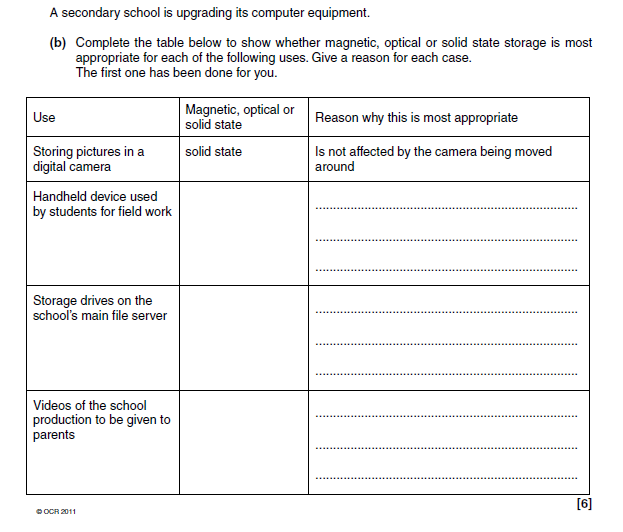
Handheld device
- Solid state
- Quick access (for instant on)/not sensitive to being moved around while used
- Magnetic
- Very Large capacity/relatively cheap
- Optical
- Cheap/Portable/Universally readable by a most computers and dedicated video disc players
1C answer
Points may include:
Input devices:
High Level Response (5/6): A good understanding with detailed descriptions of a range of relevant input as well as output devices; The information will be presented in a structured and coherent form. There will be few if any errors in spelling, grammar and punctuation. Technical terms will be used appropriately and correctly.
Input devices:
- Puff-suck switch: allows mobility impaired users to control eg clicking a mouse, by sucking or blowing through a tube
- Simplified/concept keyboards eg for Braille, or larger keys
- Eye tracking input – Camera is used to follow the users eye movements and use these to control eg movement of mouse on screen.
- Braille printer – print documents on paper in braille as raised bumps. Some braillers have plastic bumps which can be raised or lowered by software, so output does not have to be on paper.
- Text to speech
- Screen magnifiers
High Level Response (5/6): A good understanding with detailed descriptions of a range of relevant input as well as output devices; The information will be presented in a structured and coherent form. There will be few if any errors in spelling, grammar and punctuation. Technical terms will be used appropriately and correctly.
2a answer
- A Database Management System/Used to manage the database
- May use SQL/allows database to be queried
- Provides facilities for creating tables/inserting data/viewing data/reporting
- Allows data structure to be independent of the program
- Allows relationships to be created between tables/Maintains integrity
- Provides security features/levels of access
More help here - DBMS explained2
2b answer
Form:
- An input screen
- Allowing chosen data items to be displayed and edited
- Uses texboxes/drop down lists/checkboxes etc…
- When edited, the changes are updated in the database
- Suitable example from shop eg enter new products
2b answer
Report:
Up to 2 marks for description and 1 mark for example
- An output of the data in a database
- A snapshot of the data at a given time/when printed
- Of specified fields/Laid out in a specified format
- Aggregates may be calculated and displayed
- Suitable example from shop eg weekly sales
Up to 2 marks for description and 1 mark for example
2ci answer
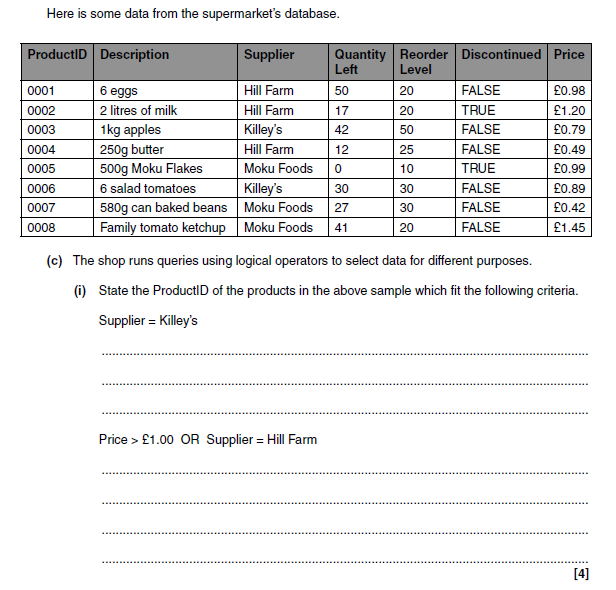
- Supplier = Killey’s.
- Answer: 0003, 0006
- Price > £1.00 OR Supplier = Hill Farm
- Answer: 0001, 0002, 0004, 0008
Award 1 mark if 0002 and 0008 are in answer
Award 1 mark if 0002 is not repeated and there are no extra answers
2cii answer
- Discontinued = False
- AND
- Quantity Left < Reorder Level
3Ai answer
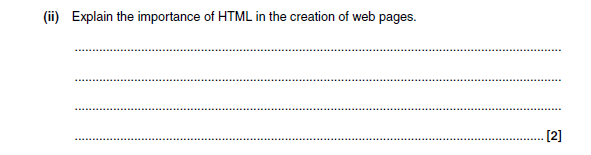
- HyperText Mark-up Language
- Text file containing the text to be displayed...
- ... uses tags which indicate how to display it
- … location of pictures/other elements to include
- ... and hyperlinks to other locations/URLS
3aii answer
- Web browser used to interpret the file and display the data correctly
- Because it is an open/accepted standard...
- ... data will display correctly on all browsers
- ... which conform to the standard
More help here - html explained
3b answer
3ci answer
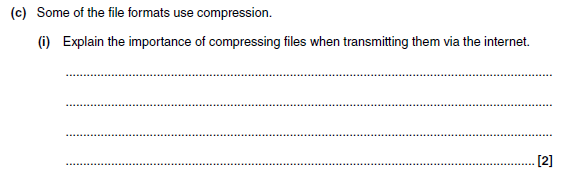
- It reduces the size of the file which needs to be transmitted
- Shortens download time
- Reduces Internet traffic (and hence probability of lost packets)
- Allows multimedia files to be streamed
More help here - compression explained
3cii answer
- In lossy compression, when the data is uncompressed it is not exactly the same as the original
- But the difference is so small that it cannot normally be noticed
- Eg music files(mp3), large resolution images for displaying on small screens.
- In lossless compression, when the data is uncompressed it is restored completely to the original file
- Eg compressed text files.
More help here - compression explained
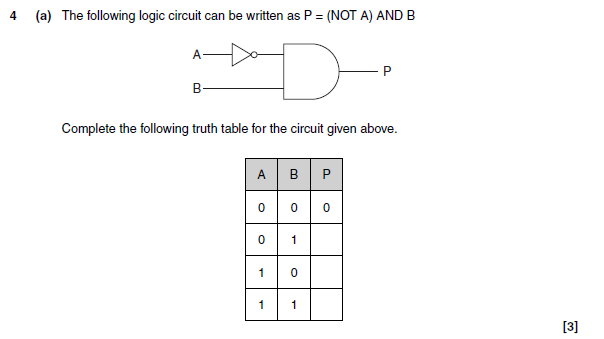
4a answer
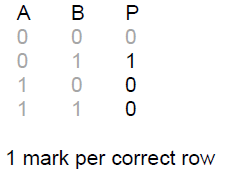
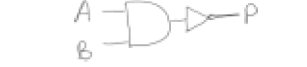
4b answer
- A B input into an AND gate
- Result from AND gate put through a NOT gate (to give P)
More help here - Use logic gates
5a answer
Antivirus
More help here - Antivirus
- Scans the computer periodically
- To check if any software has been installed which contains code that may harm the computer
- Removes/quarantines these programs / notifies the user
- Prevents these programs from being installed
- Protects the computer by preventing important files (eg the boot sector or operating system) from being changed
More help here - Antivirus
5b answer
Disk defragmenter
More help here - Disk defrag explained
- Moves (parts of) of files around so that all parts of a file are stored together (allowing files to be accessed more quickly)
- Free space is collected together (allowing large files to be saved easily)
More help here - Disk defrag explained
6a answer
- 6 * 16 (= 96) / 10 (for A)
- 106
More help here -
6b answer
6c answer
6d answer
- Hex numbers are shorter/more memorable than equivalent binary numbers..
- ... and can easily be converted to and from binary...
- ... as each hex digit corresponds to 4 binary digits
- (accept diagram)
More help here - What is hex
7ai answer
Constant: Pi
Variables: WheelSize, Circumference
Variables: WheelSize, Circumference
7aii answer
- The value of a constant is set when the constant is declared
- The value of a variable is set while the program is running
- The value of a constant cannot be changed once the program is running/can only be set at design time
- A variable has no value at design time
More help here - Variables explained
7b answer
8 answer
Points may include:
High Level Response (5/6): A good understanding with detailed descriptions of the measures and policies, explaining how they help privacy and security; The information will be presented in a structured and coherent form. There will be few, if any, errors in spelling, grammar and punctuation. Technical terms will be used appropriately and correctly.
- Physical security measures – computers/servers in locked rooms, lock down cables for laptops
- Firewalls – allow only authorised access to the network / only authorised users/programs to share data out of the network
- User groups/access levels – different users are given rights to different data according their responsibility/need to protect privacy
- Passwords enforced. Should be strong and changed regularly. Ensures privacy and protects files being accessed by malicious hackers
- Encryption of data on network
- WiFi access security if they use WiFi
- Get employees to sign an acceptable use policy as part of their contract to ensure they do not put the data at risk of corruption/abide by data protection legislation/do not give the data to third parties etc.
High Level Response (5/6): A good understanding with detailed descriptions of the measures and policies, explaining how they help privacy and security; The information will be presented in a structured and coherent form. There will be few, if any, errors in spelling, grammar and punctuation. Technical terms will be used appropriately and correctly.
9answer
Example:
BEGIN
Input RealAge
IF RealAge <= 2
DogYears = RealAge * 12
ELSE
ExtraYears = RealAge – 2
DogYears = 24 + ExtraYears * 6
END IF
END
Award marks for an algorithm which:
BEGIN
Input RealAge
IF RealAge <= 2
DogYears = RealAge * 12
ELSE
ExtraYears = RealAge – 2
DogYears = 24 + ExtraYears * 6
END IF
END
Award marks for an algorithm which:
- Allows real age to be input
- If age <=2, multiply real age by 12
- Works out extra years (real age – 2) …
- … multiply by 6
- … adds 24 (for the first 2 years)